Interim Demonstrator
SYNERGIA Interim Demonstrator
Introduction
The Interim Demonstration of the SDTaP project SYNERGIA was held at the end of January, when the progress on the project’s innovative security solutions for IoT was presented to security experts from various industries. The main aim was to receive critical feedback for validating both the approaches taken so far, as well as the future direction of developments towards the Final Demonstration and beyond the project end.
The event started with an introduction from Dr. Theo Spyridopoulos:
Advisors
Due to Covid, the event was mainly conducted online; with security experts from WMG, BT, Nquiring Minds, Angoka, and Cardiff University attending and providing valuable feedback and advice.
Further meetings of the expert Advisory Group are planned in mid-June and mid-September and the project prepares our Final Demonstration.
If you would like to have more details of the SYNERGIA project, or attend the final public demonstration in October 22, please let us know at synergia-steering@toshiba-bril.com.
Demonstrations of security solutions
Backend/Core network (Work Package 4)
SYNERGIA is based on a three-tier architecture consisting of Backend, Edge, and Endpoints (including various sensors). The Endpoint is configured by one of the Edges, which is received from the Backend.
The Backend provides services to the Edge and Endpoint devices in a reliable, scalable, and secure manner. Further, the Backend can deploy applications that can access device hardware (such as several radios) present on the Edge nodes. The Backend also provides secure configuration such as Edge device settings (e.g. network, radio, allowed/denied list of endpoints etc.) and Endpoint device settings (e.g. encryption keys, MQTT server details, etc.). Further, the Backend also provides the capability to receive data from Endpoints (MQTT/Web sockets server) and store it (InfluxDB database). The Backend is built mainly on Toshiba’s UMBRELLA IoT project infrastructure.
The SYNERGIA platform enables specific but different roles: Endpoint/Edge OEM, Endpoint Owner, Platform Operator, service and dataflow owner, and security expert. From the hardware perspective, the Backend runs on a server; the Edge tier comprises small board computers (SBCs) with multiple radios, the Endpoint tier, consists of multiple sensors integrated into numerous wireless Endoints.
At the Interim Demonstration we showcased several of the project’s innovations: detection of malicious activity using Federated Learning (FL), secure configuration of the Edge and Endpoint devices, and the use-cases where SYNERGIA solutions can be deployed.
Secure Configuration Management at the Edge (Work Package 3)
Secure configuration of the Edge devices including the Edge-resident data-pipelines, and the connected Endpoints was demonstrated for applications such as multi-tenancy buildings, with the ability for users to configure up their own Endpoints, create specialized Edge-resident data processing pipelines, and securely share data from these with other users in a highly controlled way.
This approach was demonstrated through three roles that act independently, but collectively control the overall state of the system: a Platform Operator that configures IoT radio network and adds other roles to the system, an Endpoint Owner that then configures their Endpoint devices and their associated data flows, and a Security Officer who is able to selectively disable Endpoints that are perceived to have become a threat to the system. We also showed how existing PKI can be used to enforce the trust model within and between these roles. This demonstration is shown in the following video.
Intrusion Detection by Federated Machine Learning (Work Package 1)
SYNERGIA’s framework for automated detection of IoT Network intrusions was showcased with a dataset including with two attack scenarios. We also demonstrated our Intrusion Detection method that uses Federated Learning (FL) and autoencoders (Detecting Network Intrusions at the Edge blog). Finally, for anomalies detected by the FL-based Intrusion Detection System with only a low confidence, we also demonstrated our human in the loop web interface that enables security experts to analyse and label the low confidence samples in the system, to continually improve the performance of Intrusion Detection System by subsequently retraining the Machine Learning model.
The video below demonstrates the generation of the intrusion dataset and the FL inference within the MAIO dashboard (MAIO). We also show the interface highlighting various visualizations to help and support an expert correctly analyses the low confidence data.
Security of Resource-Constrained Endpoints (Work Package 2)
SYNERGIA demonstrated innovative security solutions for highly resource-constrained Endpoint devices. Two session key exchange approaches were shown that depend on pairwise pre-shared symmetric keys between the Endpoint and the Edge/Backend. The first session key exchange uses key transport, which is more appropriate for severely constrained devices. The second approach uses the Elliptical Curve Diffie-Hellman key agreement for devices with more computational capabilities. Using a network analyser, SYNERGIA demonstrated that the wireless Endpoint packets are encrypted from the Endpoint to the Edge device (message integrity is also provided using authentication codes). Vital for severely resource-constrained devices, SYNERGIA also demonstrated the energy usage of these key exchange approaches using several power monitoring tools.
Use Cases (Work Package 5)
The security solutions developed in SYNERGIA are demonstrated on an UMBRELLA-based IoT deployment that can provide a secure platform for multi-tenancy smart building applications. The platform is deployed at Future Space, a space managed by Oxford Innovation, and follows the three-tier architecture including battery-powered Endpoints with a number of environmental monitoring sensors scattered in various locations, UMBRELLA Edge devices in two locations and a Backend server described earlier.
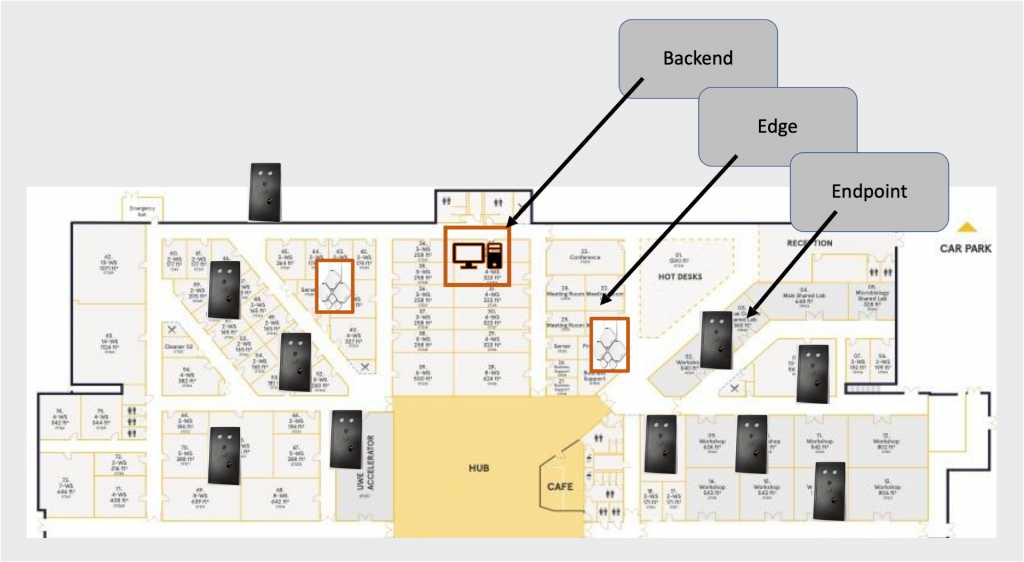
We are currently planning to have our first deployment ready by April 2022. Toshiba, the University of Bristol and MAC Ltd provide more information around the deployment and the Endpoint sensors in following video:
Conclusion
Feedback from our expert advisors was highly valuable in guiding our future developments, and our plans for commercial exploitation of our innovations.
At least two more meetings of the expert Advisory Group were agreed.
If you would like to have more details of the SYNERGIA project, or attend the final public demonstration in October 22, please let us know at synergia-steering@toshiba-bril.com.